Azure AD B2C Tip: Make sure you explicitly grant permissions between apps with delegated permissions
I’ve been continuing my journey to deepen my understanding of Active Directory and Active Directory B2C and establish best practices and a reference architecture for creating automated integration tests for a Web API protected by either Azure Active Directory or Azure Active Directory B2C.
I wanted to write about an issue that I encountered when attempting to obtain a bearer token by directly hitting Azure Active Directory’s OAuth2 Token Endpoint to attach onto requests made to a WebAPI.
While monitoring the traffic in Fiddler I discovered that I was receiving 400 bad request responses and inside the response body I discovered the error code: “AADSTS65001: The user or administrator has not consented to use the application with ID
I was at a loss, what could this possibly mean? It turns out the solution was a simple action that needed to be taken from the portal.
Before, I get to that, let me share the structure of the Trust Relationship I created within Azure Active Directory.
I have a Web API / Web App called “WebApplicationB2C” that is where I have the WebAPI that I would like to hit from my unit test project.
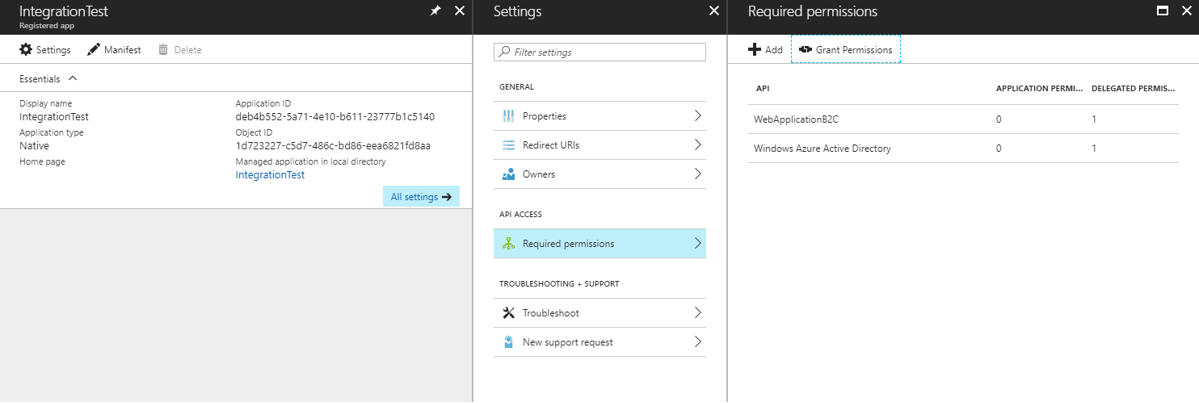
I have a Native App called “IntegrationTest” that is what I am going to use to obtain the bearer token within my unit test project.
My application registrations for this setup look like this:

You can see that I’ve established “Required Permissions” of the “IntegrationTest” to have access to the “WebApplicationB2C” application:
In my unit test project I attempt to make the following OAuth2 call:
The exact response I got back when observing the response from Azure Active Directory in Fiddler was this:
{"error":"invalid_grant","error_description":"AADSTS65001: The user or administrator has not consented to use the application with ID 'deb4b552-5a71-4e10-b611-23777b1c5140' named 'WebApplicationB2C'. Send an interactive authorization request for this user and resource.rnTrace ID: 13bb79c1-58b0-45c5-b663-7385ff1a0100rnCorrelation ID: fea7ce95-41e4-4aa8-af11-90e5529aca48rnTimestamp: 2017-11-11 02:13:11Z","error_codes":[65001],"timestamp":"2017-11-11 02:13:11Z","trace_id":"13bb79c1-58b0-45c5-b663-7385ff1a0100","correlation_id":"fea7ce95-41e4-4aa8-af11-90e5529aca48"}
The Azure Active Directory error follows this template:
“AADSTS65001: The user or administrator has not consented to use the application with ID '<GUID>' named '<AppName>'. Send an interactive authorization request for this user and resource”
I simply went back to “IntegrationTest” app and clicked the “Grant Permissions” button. This effectively authorized the application by me, the Administrator.