Terraform + Azure DevOps Environment Variable Piping Tips
When establishing good security processes around your software release pipeline it’s important to ensure that secrets are handled with care. As a best practice, I always ensure secrets that need to be used in a CI / CD pipeline are stored in Key Vault and imported into an Azure DevOps Variable Group. This allows the secrets to be reused across multiple pipelines and ensures they are stored and accessed securely.
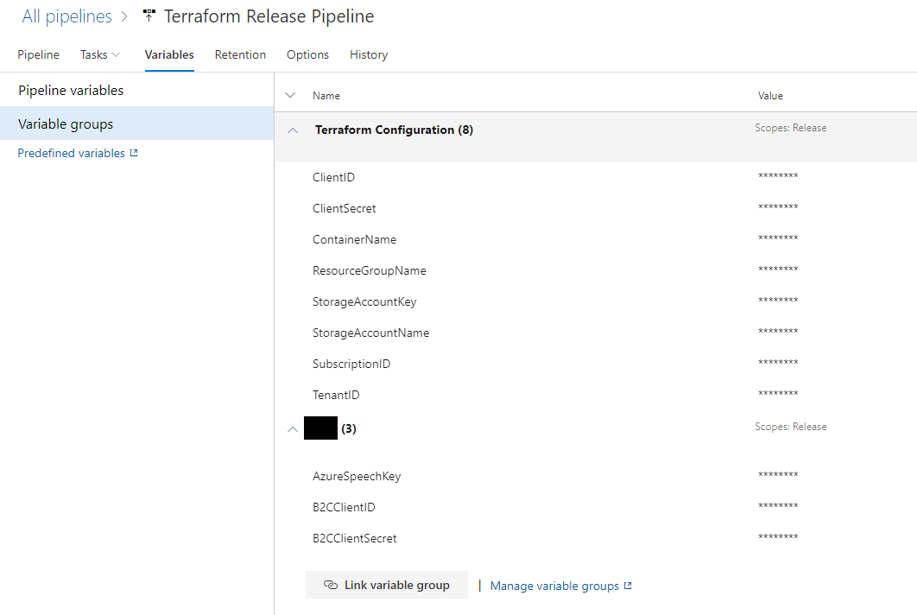
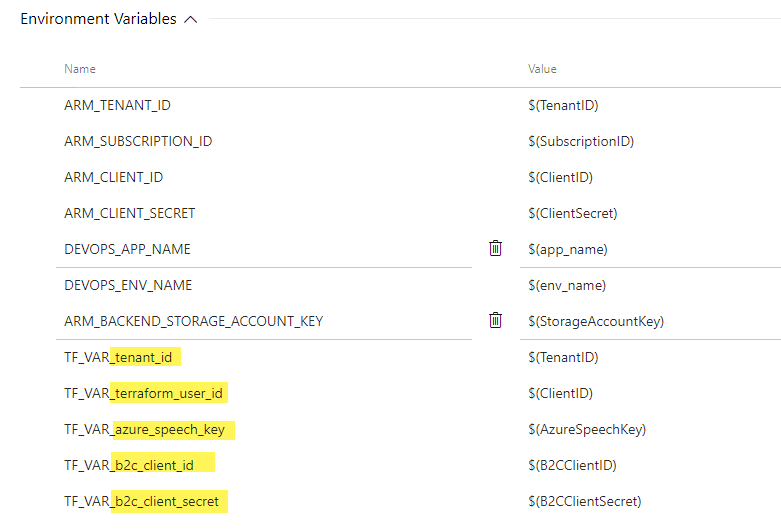
When piping them into a Terraform process. Another important thing is to remember the following:
- Terraform input variables are CASE SENSITIVE
- Terraform allows input variables to be imported from environment variables prefixed with “TF_VAR_”. Yes all caps. No deviations.
Due to conventions, usually my Terraform variables are setup as lowercase, underscore delimited word segments. I was just banging my head against this for an embaressingling long amount of time and thought I would share the reminder. Make sure that your environment variable mappings you create in AzureDevOps take into account the case sensitive nature of Terraform and when you construct your “TF_VAR_{variable_name}” environment variables you need to ensure that the case matches EXACTLY to what Terraform is expecting inside the {variable_name} piece. Otherwise, you will be plagued with “{something-something} must not be empty}” errors from your Terraform apply command output!