The Foundations of Infrastructure as Code: Managing Environments with Terraform
Infrastructure as Code (IaC) has revolutionized how we design, deploy, and manage cloud environments. By treating infrastructure configuration as version-controlled code, IaC empowers teams to create repeatable, reliable processes for building and managing complex systems. At its core, IaC is not just a toolset but a mindset that leverages principles of software development to manage environments with precision and scalability. This article explores the theoretical underpinnings of IaC, focusing on Terraform as a prime example. We’ll dive into the key elements that make Terraform an essential tool for managing environments and examine how these elements fit into the broader context of infrastructure management.
The Building Blocks of Infrastructure-as-Code
Effective infrastructure management with IaC depends on understanding several interconnected components. Each plays a distinct role in translating developer intent into operational environments.
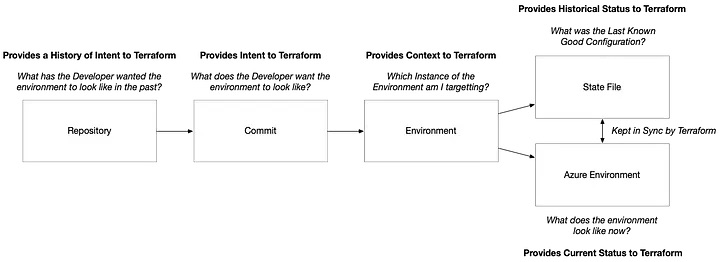
Repository: The History of Intent
At its simplest, a repository is where your infrastructure code lives, but its importance goes far deeper. It serves as a historical record of your infrastructure’s evolution, capturing every change and decision made along the way.
This historical perspective is invaluable for debugging, auditing, and understanding the rationale behind previous decisions. By leveraging version control, teams can track changes, roll back to previous states, and collaborate seamlessly on infrastructure management.
What has the Developer wanted the environment to look like in the past?
Commit: The Manifestation of Intent
A commit represents the developer’s current intent — what they want the environment to look like in its ideal state. This intent drives Terraform’s planning and execution process, serving as the basis for determining what changes are required to bring the environment into alignment with the desired configuration. Each commit is effectively a declaration of the future state, forming the bridge between the human understanding of the infrastructure and Terraform’s execution engine.
What does the Developer want the environment to look like?
Environment: What am I targetting?
Environments provide essential context for Terraform, specifying which instance of the configuration is being managed. Whether it’s dev, test, prod, or specialized setups like QA or load testing, this context ensures Terraform operates on the correct scope of resources.
To manage environments effectively, I typically divide the environment context into two parts:
- Application Name: A unifying identifier that spans all instances of the configuration.
- Environment Name: A unique value that differentiates deployments (e.g., dev, test, prod).
For more complex architectures, particularly microservices, you might extend this context to include an additional identifier for the specific service being deployed. This segmentation provides flexibility, enabling teams to manage independently deployable units without overwhelming naming conventions.
Which Instance of the Environment am I targetting?
State File: The Historical Record
The state file is Terraform’s memory of the last known good configuration. It’s where Terraform stores details about the resources it manages, including their current attributes and relationships. The state file answers the question: What was the infrastructure’s status when Terraform last applied changes? This historical record is crucial for ensuring consistency and determining deltas between the desired state (as defined in the code) and the actual state (as observed in the environment). Without a reliable state file, Terraform would lack the context needed to make informed changes.
What was the Last Known Good Configuration?
Your Actual Environment: The Current State
While the state file provides a snapshot of the past, the actual environment (whether it’s on Azure, AWS, or wherever) reflects the present. Terraform compares the desired state (from your code) with the current state (in Azure) to generate a plan for reconciling any differences against the historical record: Terraform State. This real-time evaluation ensures that your infrastructure aligns with your declared intent while avoiding unnecessary changes.
What does the environment look like now?
Infrastructure-as-Code: Context Matters
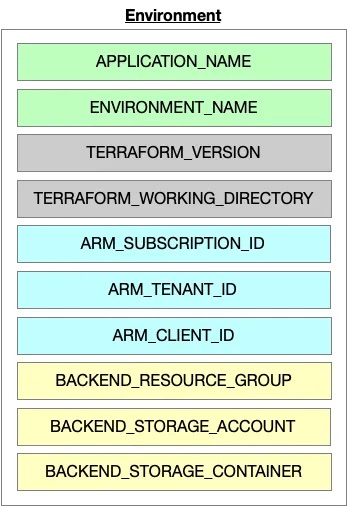
To implement Infrastructure-as-Code, you need to account for four key contexts. These contexts form the scaffolding of your environments and drive Terraform’s behavior:
- Environment Context
- Terraform Runtime Configuration
- Authentication Context
- Backend Context
Environment Context
The environment context specifies the unique instance of the configuration to provision. This is a generic concept that applies across all platforms. By defining application and environment names, you create a structured framework for managing resources.
For example:
- Application:
my-web-app - Environment:
dev
Together, these components form a unique identifier, ensuring that resources are deployed consistently across environments. In more complex setups, you might also include a service identifier to account for microservices architectures.
Terraform Runtime Configuration
The runtime configuration tells Terraform what to do and where to do it. This includes:
- Terraform Version: Ensures compatibility and consistent behavior across environments.
- Working Directory: Points Terraform to the directory containing your configuration files. These simple but critical settings are prerequisites for Terraform’s operation.
Authentication Context
The authentication context defines how Terraform connects to the target platform. This is one area where cloud-specific considerations come into play. For example:
- Azure: Terraform may use the azurerm, azapi, or azuread providers, all of which share a common authentication mechanism through Entra ID.
- AWS: The aws and awscc providers share authentication through AWS’s identity service, AWS IAM. Defining and understanding your authentication context is essential, especially when troubleshooting issues.
Backend Context
The backend context determines where Terraform stores its state files. While state files don’t need to match the target platform, many cloud providers offer dedicated services for this purpose:
- Azure Blob Storage for Azure environments
- AWS S3 for AWS environments
Remote State is absolutely essential when executing Infrastructure-as-Code at scale. Therefore, you should always plan for a Backend Context.
Where the Rubber Hits the Road
Infrastructure as Code is more than a technical framework — it’s a new way of thinking about environment management. It transforms infrastructure from a collection of manually managed resources into a coherent, codified system. By leveraging principles of version control, context-aware configuration, and automation, it enables teams to achieve greater consistency, reliability, and scalability.
These four contexts will ultimately be broken down into tangible elements within code and configuration — stored, for example, in a GitHub Environment. Each group of variables and their values represent the critical context that Terraform needs in order to fulfill it’s mission.
Infrastructure-as-Code represents a paradigm shift in environment management. Instead of manual configurations or ad-hoc processes, IaC provides a structured, code-first approach that integrates seamlessly with modern development practices. By understanding the role of repositories, each commit, a GitHub Environment, the Terraform State File, and your actual environment out in the cloud of your choice, you can effectively manage infrastructure with Terraform.
These components, combined with context-specific configurations like runtime, authentication, and backend setup, form the foundation for scalable, predictable infrastructure management. Whether you’re automating a simple development environment or orchestrating a multi-cloud deployment, embracing Infrastructure-as-Code enables you to build systems that are both resilient and adaptable to future needs.