Adventures in AAD B2C with UWP WinUI 3 SDK: Part 3
So we went about setup up, breaking and re-setting up Microsoft Account logins for our AAD B2C WinUI 3 App. Now let’s try enabling an Azure Active Directory Tenant to allow us to login to our B2C app using our organizational identities.
I follow this documentation to setup the new IdP inside my B2C tenant.
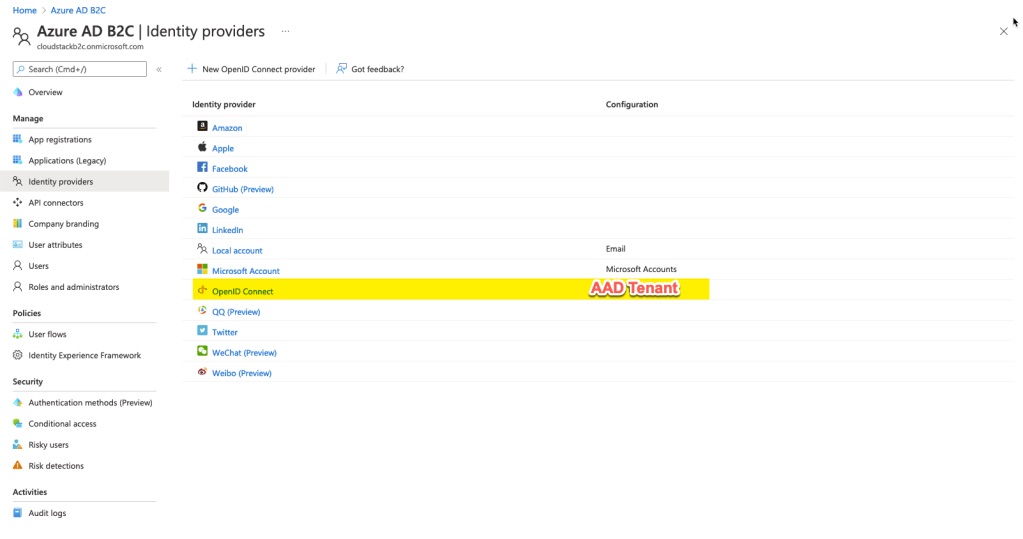
Finally, I add the OpenID Connect IdP to my User Flow for Sign In / Sign Up.
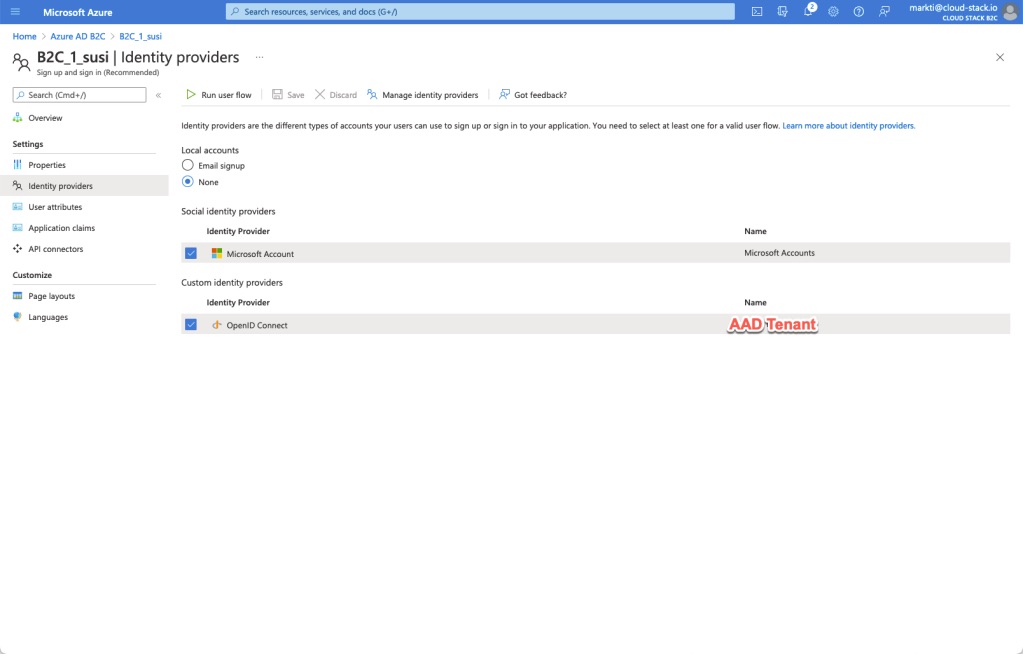
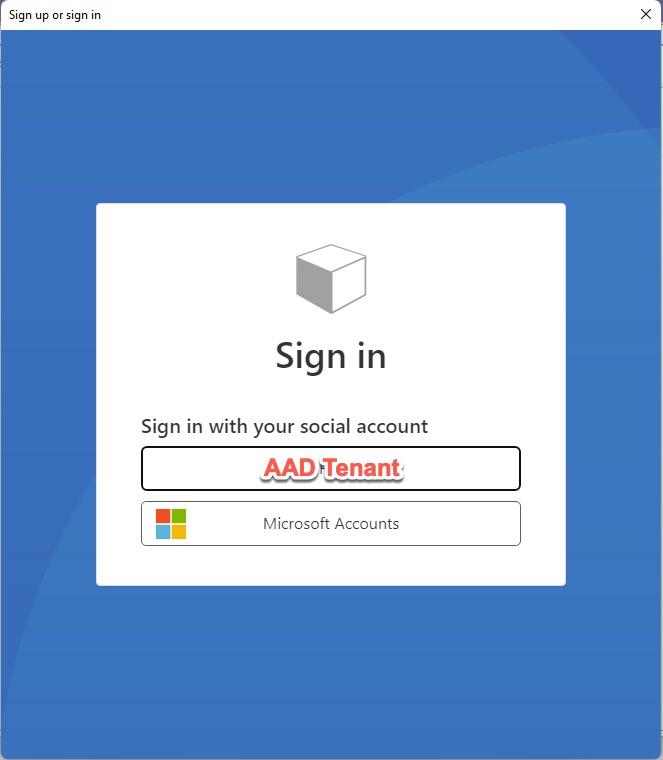
Now I see two options for my users:
- The AAD Tenant that I just setup and
- Microsoft Accounts (for consumer users)
Even the MFA policy of the AAD tenant magically works.
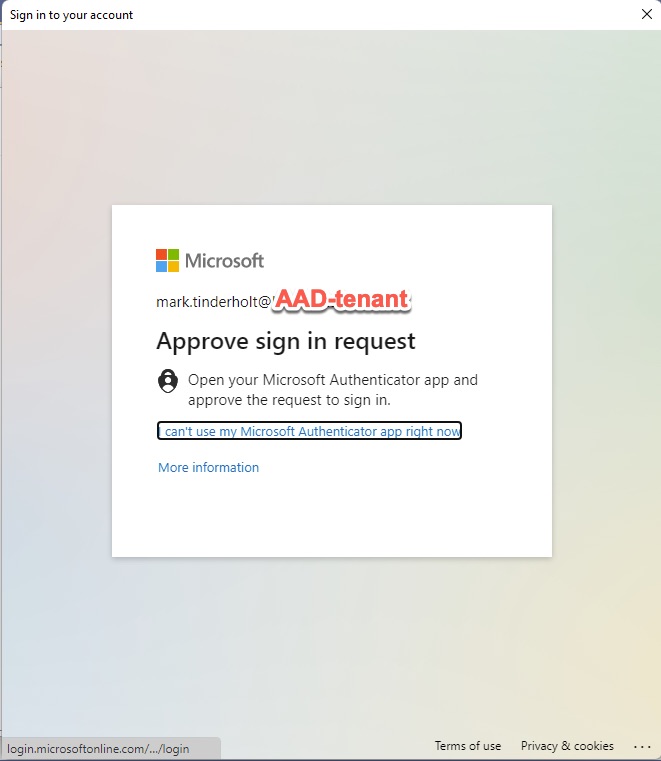
You will need to register your organization in order for the obligatory “unverified” warning to go away and I’m sure you’ve named your App Registration something more exciting than “Sample Mobile App AAD”.
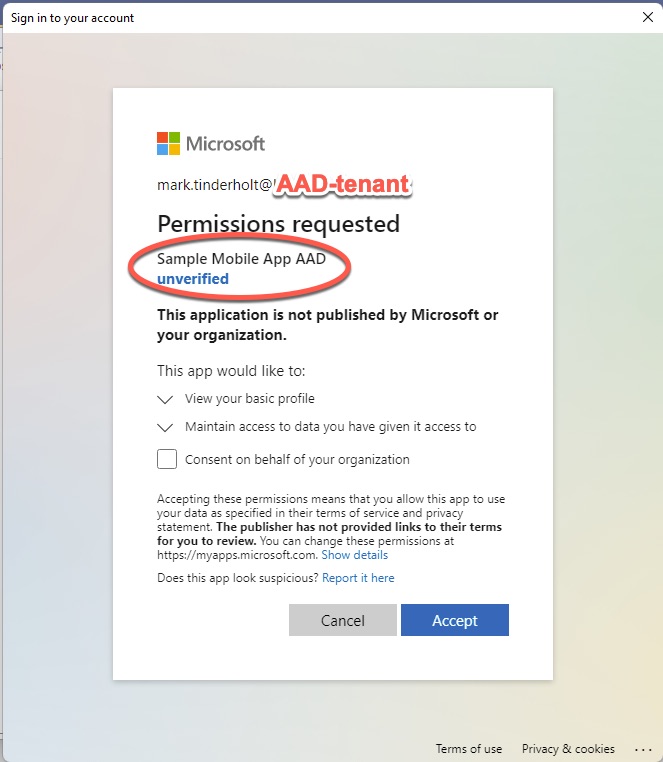
It’s important to note that the application we are talking to here is NOT the B2C app but the App Registration that we setup in our AAD tenant that has a client secret authentication with the 3rd party AAD Tenant.
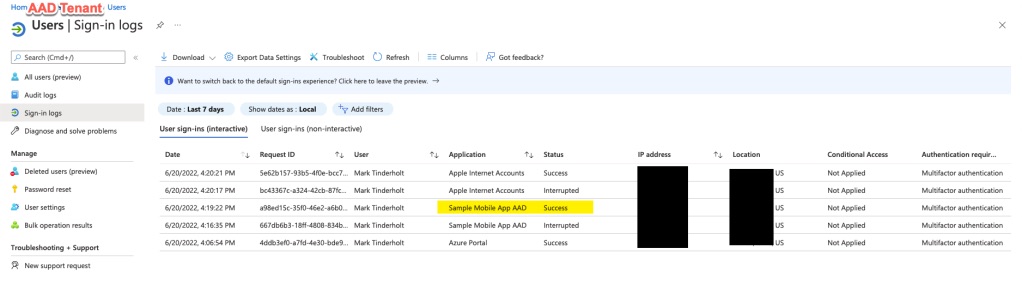
The login activity will show up in the 3rd party activity log like this:
the login activity shows the Token Type of “Azure AD”
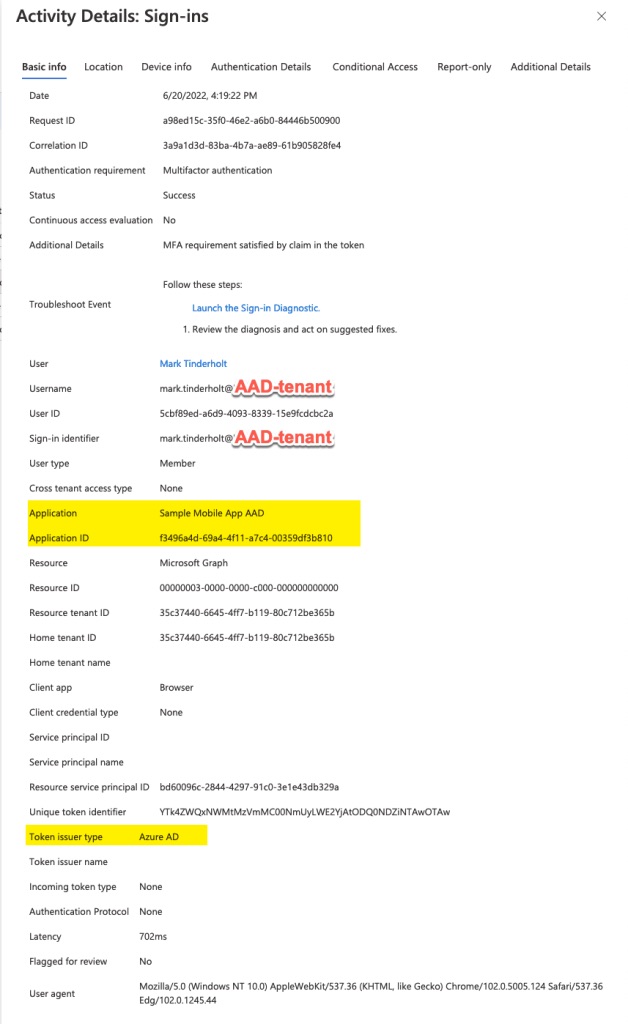
I’m not sure what happens when I do this from a mobile device. I would expect a “device ID” to show up.