Setting up Key Vault secured Pipelines with Azure DevOps
One of the first things you need to do when setting up a new Azure DevOps pipeline is to pull secrets from Azure Key Vault into a Variable Group. Variable Groups can be used by your project to setup how things like Terraform in your pipelines will authenticate themselves with Azure, AWS, or GCP.
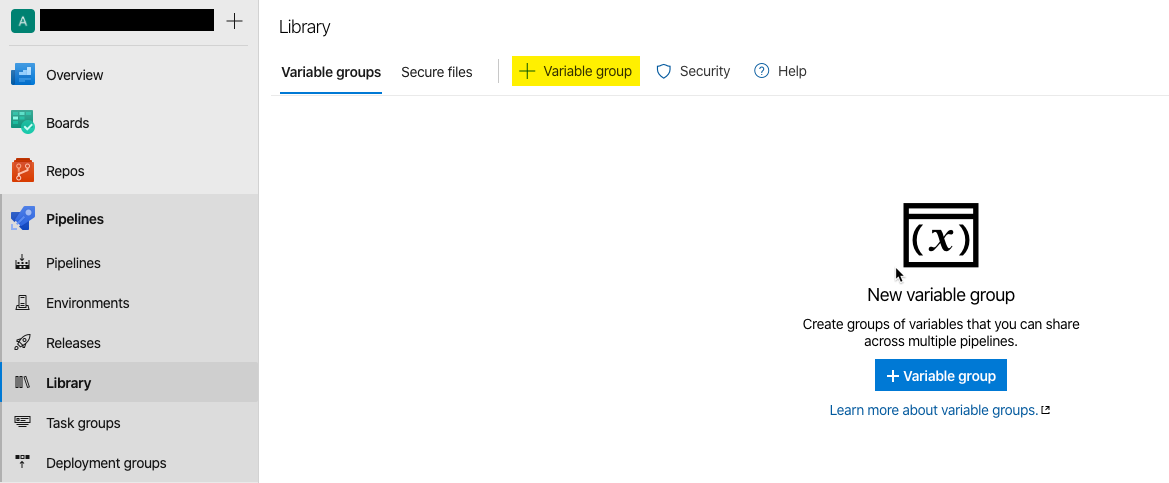
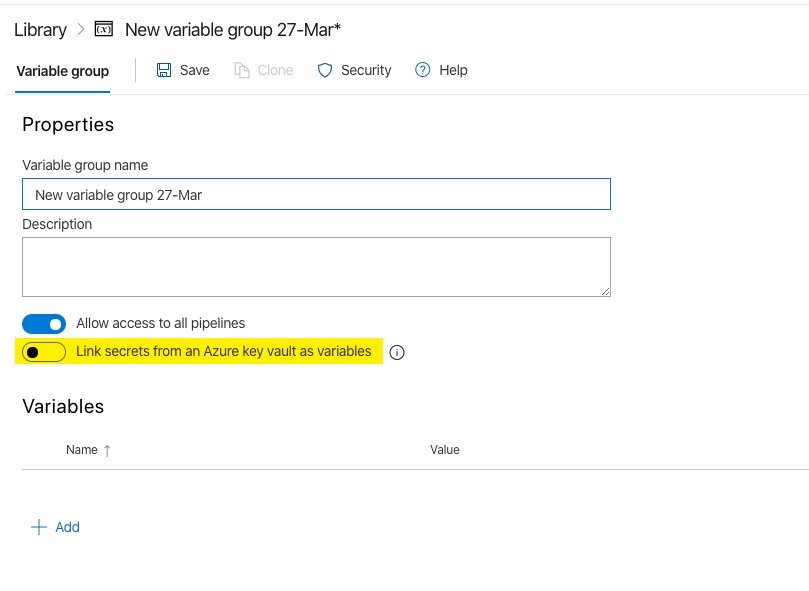
By default, when setting up a Variable Group, you can manually add them. The problem with this is that they will only be usable within this project. If you want to use them across projects you should use “Link secrets from an Azure Key Vault”.
Once you check this flag you simply need to select the Subscription and the Key Vault you want to pull from.
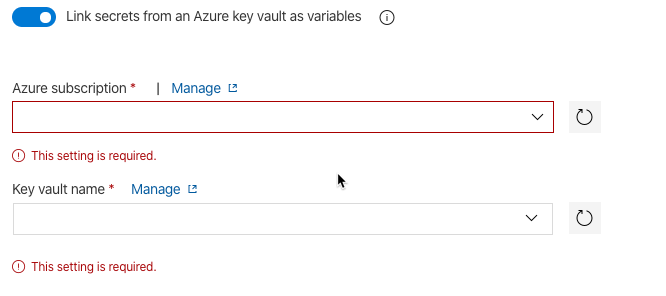
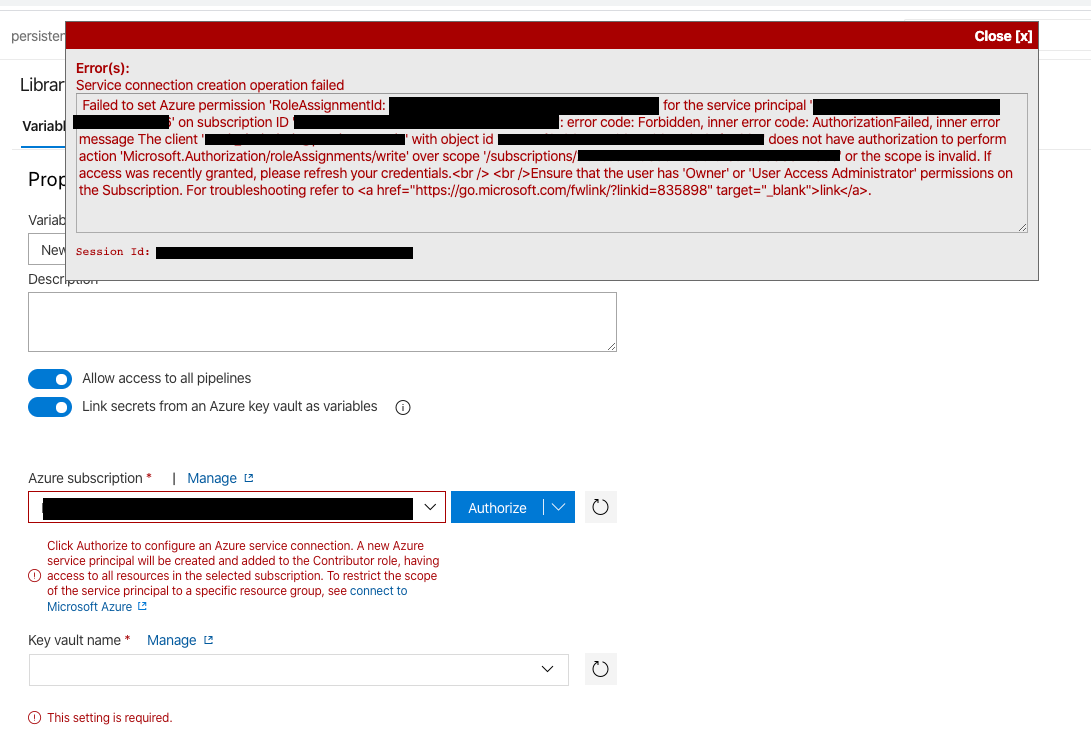
However, in order for Azure DevOps to pull Key Vault secrets you will need to setup a service principal in Azure Active Directory to allow that. If you are an Azure Active Directory Global Administrator (or have sufficient privledges to provision Security Principals within your Azure AD tenant) then you can click Authorize and it will automatically setup this Service Principal and connect to the Azure Subscription with it.
If not, you will get this error:
After that has been done you can manually create an Azure Resource Manager connection:
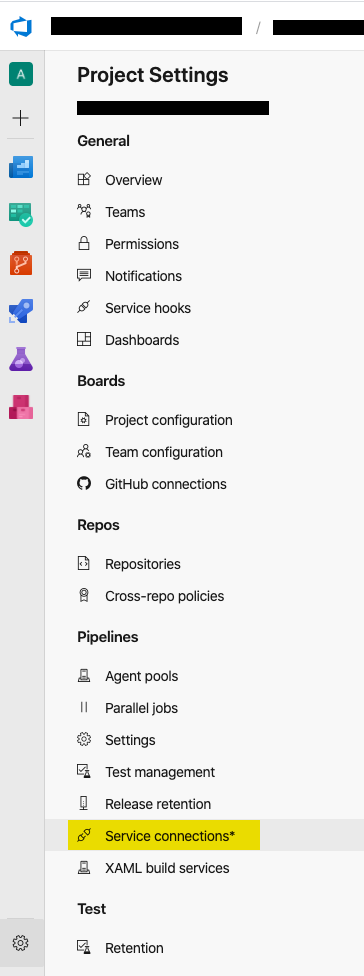
Go to project settings and select “Service connections”
Then select “Azure Resource Manager”
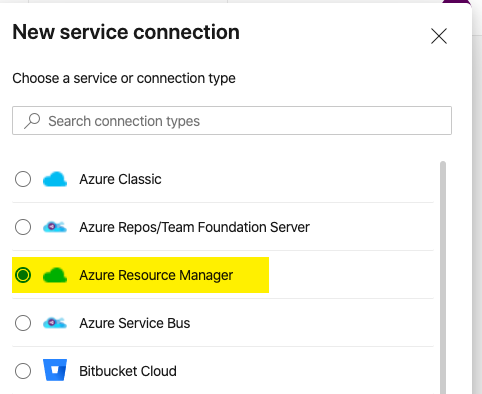
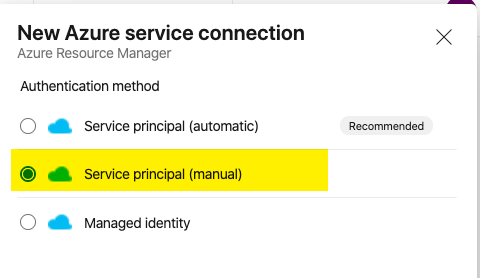
Then select Service Principal (manual). Service Principal (automatic) will only work if your currently a Global Administrator or have rights to provision Service Principals and assign RBACs (Role Based Access Controls) to them.